Additionally, EFF has deprecated use of aptitude/yum/dnf/etc package managers for deploying Certbot on Debian-based systems. Instead, they recommend use of Snap.
At work I recently collaborated with our hosting provider to move our company website to a version of cPanel. Up until this time, there has been no way of running our site on SSL/TLS, and it’s been quite frustrating, having discovered LetsEncrypt and its ease of use. Basically, with this certificate signer, I have no reason to actually figure out the handshaking and signing process as was required in old command-line versions of SSL.
Well, our hosting provider’s version of cPanel has not really been expanded to allow for LetsEncrypt, even though multiple people on the cPanel forums say there’s a plugin available. Seems they don’t mind forcing me to pay another fee on top of everything to get an annual signature from the two default signers they had enabled in the system.
This made me wonder, and think, well CertBot, which generates the certificates and private keys and runs the signing requests automatically, always talked about this “cert only” option, and here on their website, I see instructions for a “manual” option as well. I thought this may have been exactly what I was looking for, since my scenario is – I have a website on a host who does not have LetsEncrypt enabled, but does allow me to upload certificates and keys from an offline source.
Here is my process of installing a LetsEncrypt SSL/TLS DV certificate on a cPanel site not equipped to generate one automatically.
Create a new certificate with any subdomains we’d need using certbot certonly -d c-pwr.com,www.c-pwr.com –manual
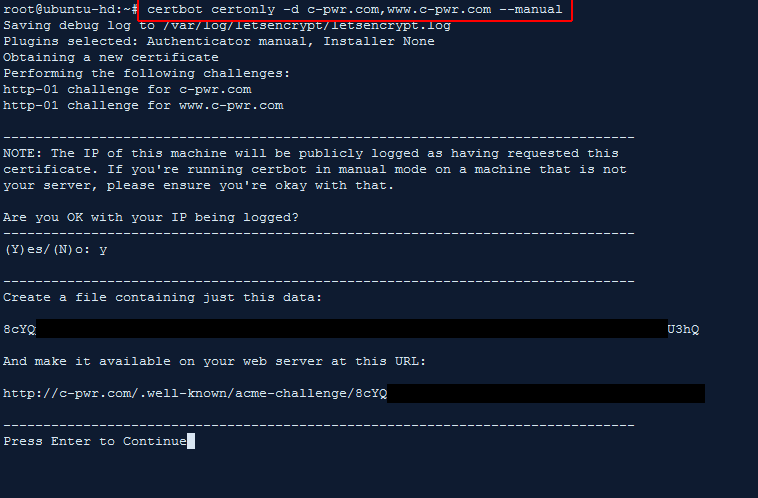
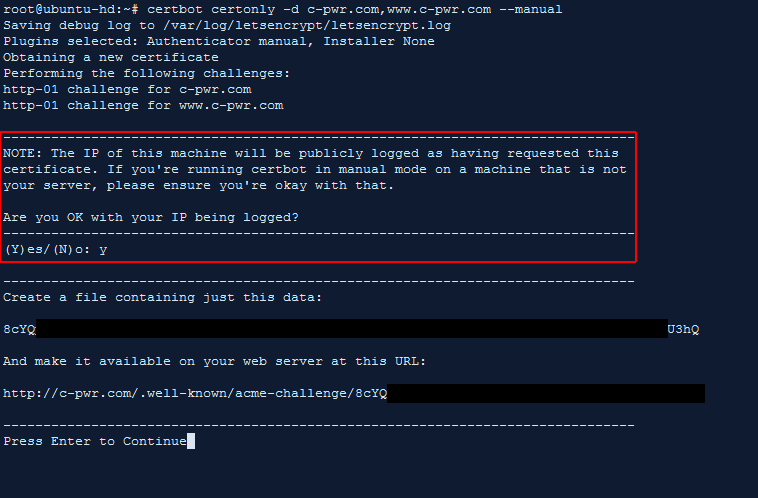
Certbot warns you that the computer’s IP you’re generating the certificate on will be shared with them, even though it’s not the server on which the cert will be installed on in the end. Type Y.
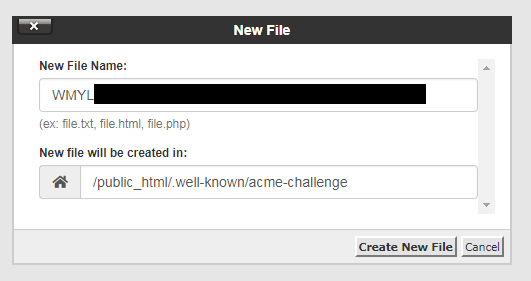
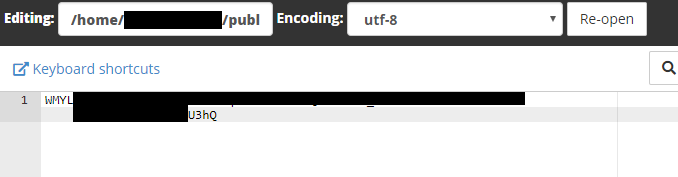
Without any “challenges” option in the original command, certbot assumes you’re using the acme challenge which involves uploading a text file to your site. Using cPanel’s file manager I simply do this.
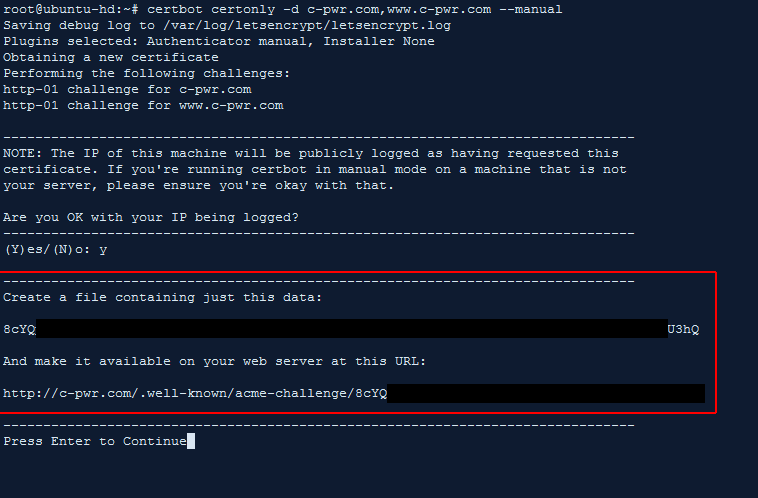
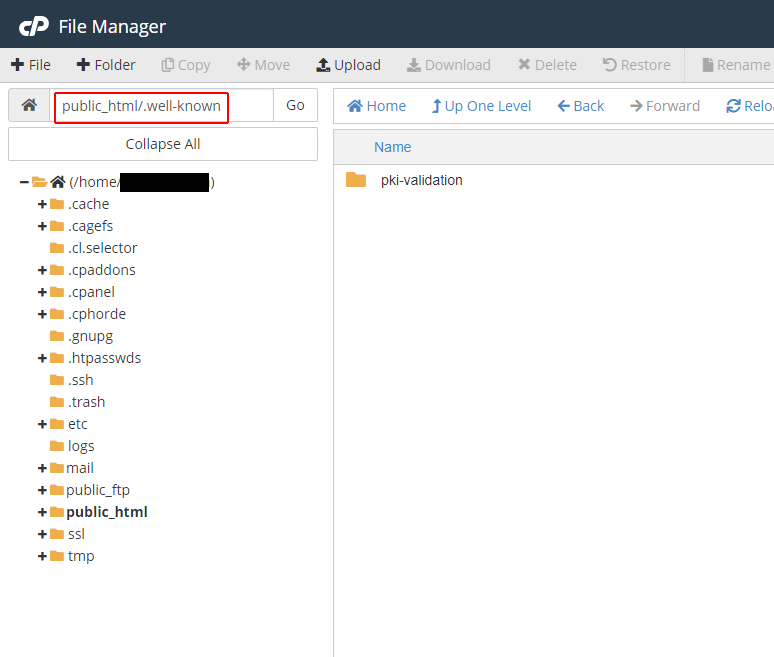
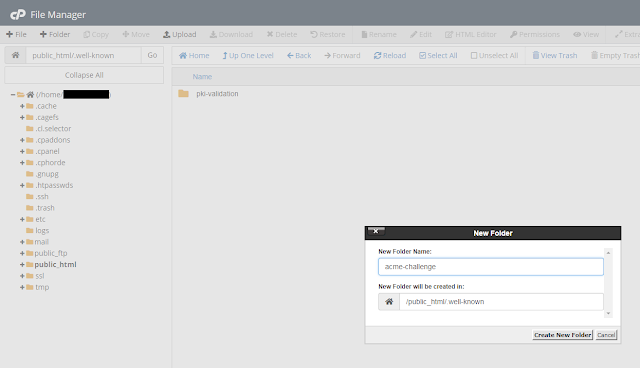
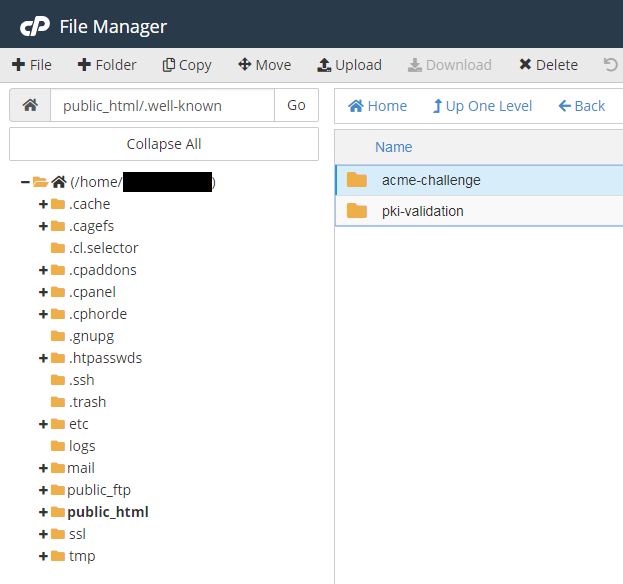
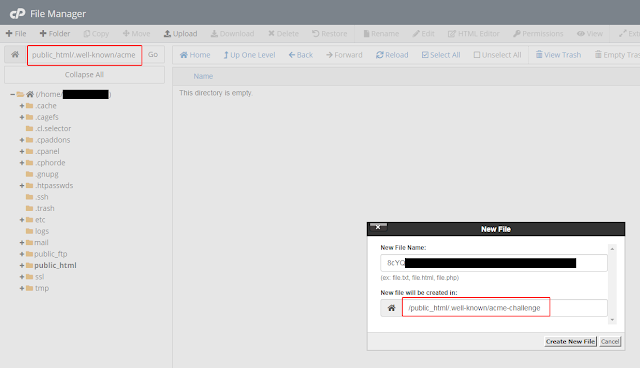
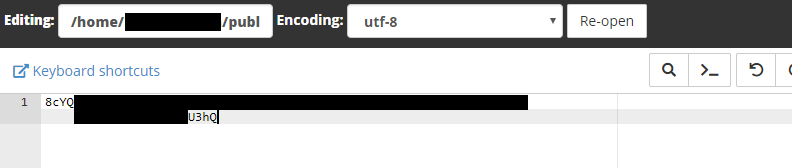
Once the first file in acme-challenges is created, certbot asks us to create another file in the same place with a different string as its contents.
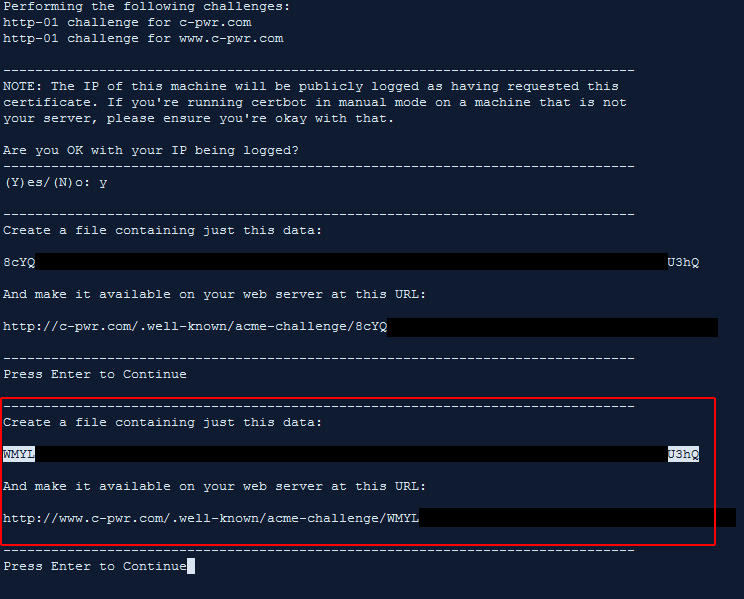
Once both files are created and saved to this location, we probably should verify that the URLs certbot is pointing to are actually visible from the public web.
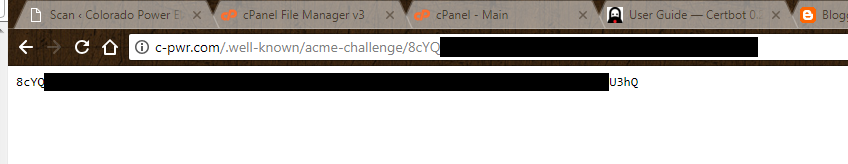
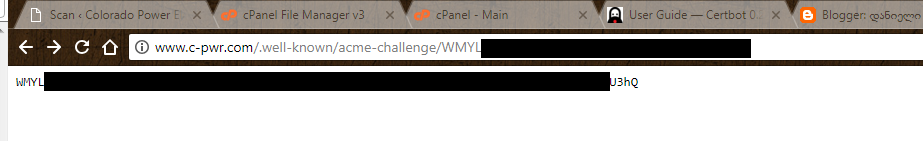
Knowing that I can access the challenge files from my browser, I assume certbot will also be able to access them, presumably from a curl command or something, so I let it continue.
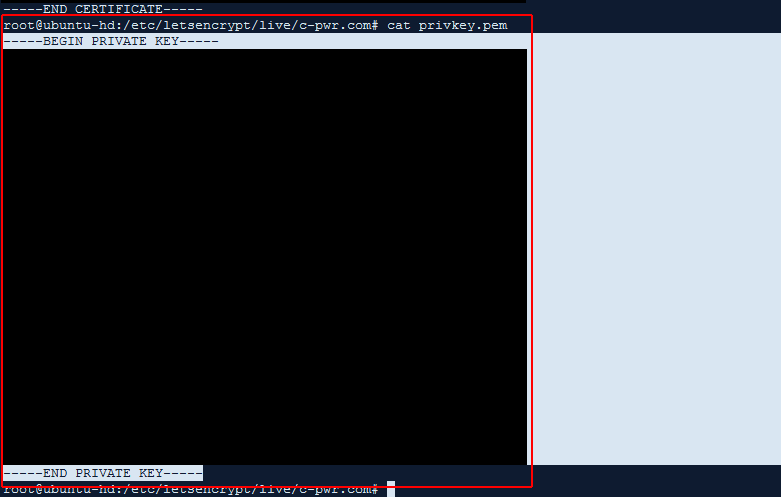
If we get the standard certbot success message, we now see that it’s created our certificate, chain and private key files in certbot’s standard location (I’m using the PPA repository through aptitude, so certbot automatically installs the latest versions of my certificates to /etc/letsencrypt/live/c-pwr.com/ , which are actually symbolic links to /etc/letsencrypt/archive/c-pwr.com/ , as every time we renew, it will archive the old files and create new ones.
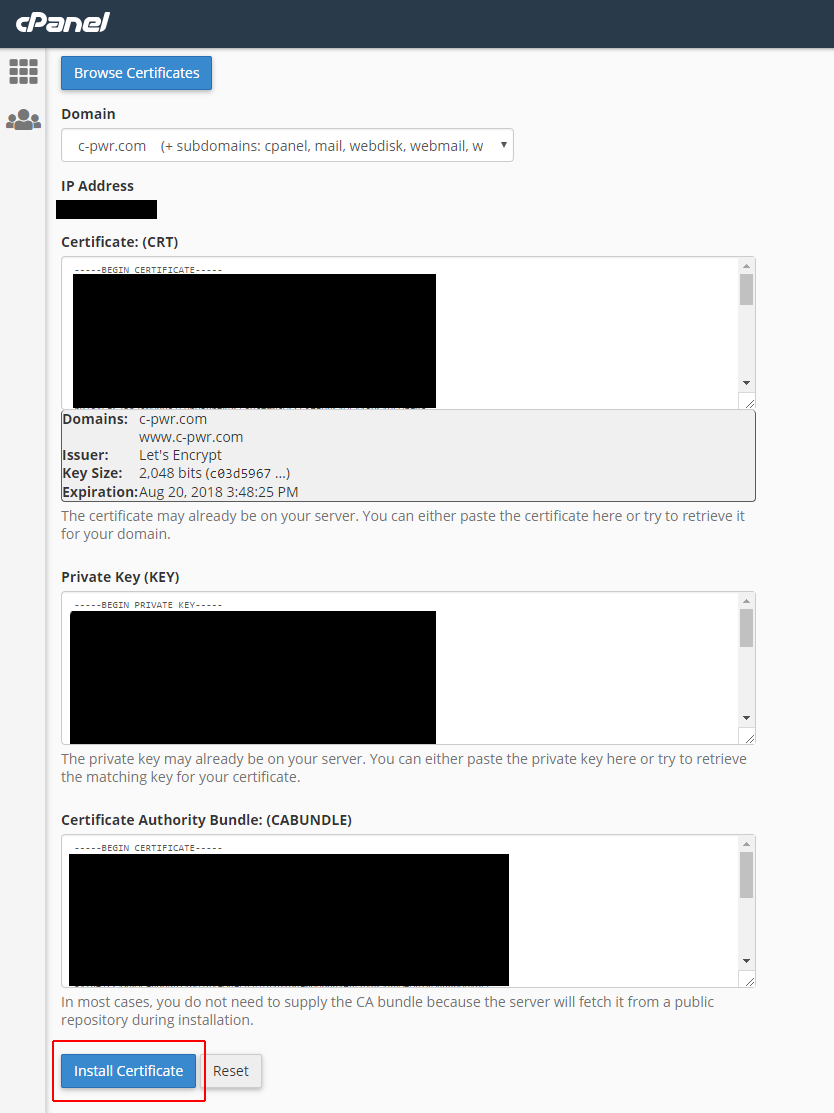
I now can copy the contents of both /etc/letsencrypt/live/c-pwr.com/cert.pem and /etc/letsencrypt/live/c-pwr.com/privkey.pem up to cPanel in their SSL interface.
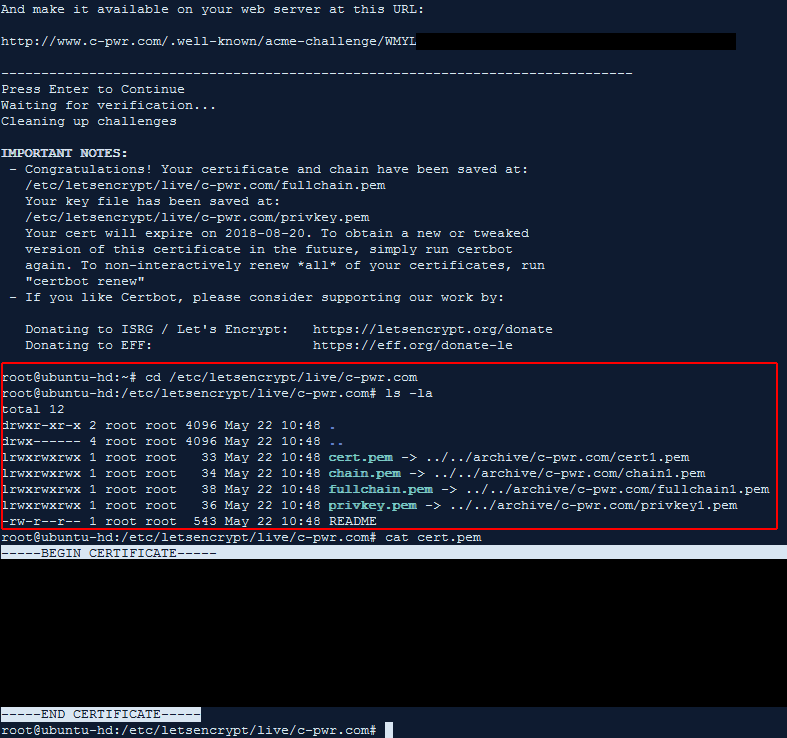
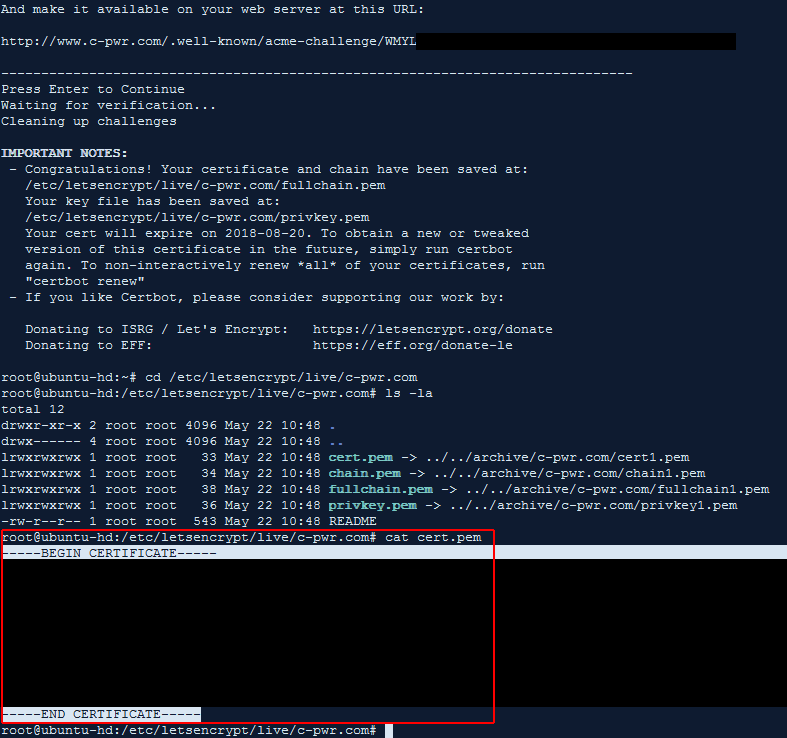
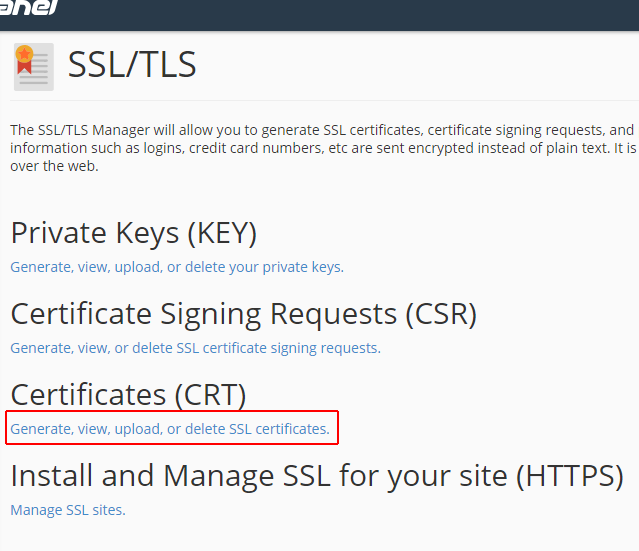
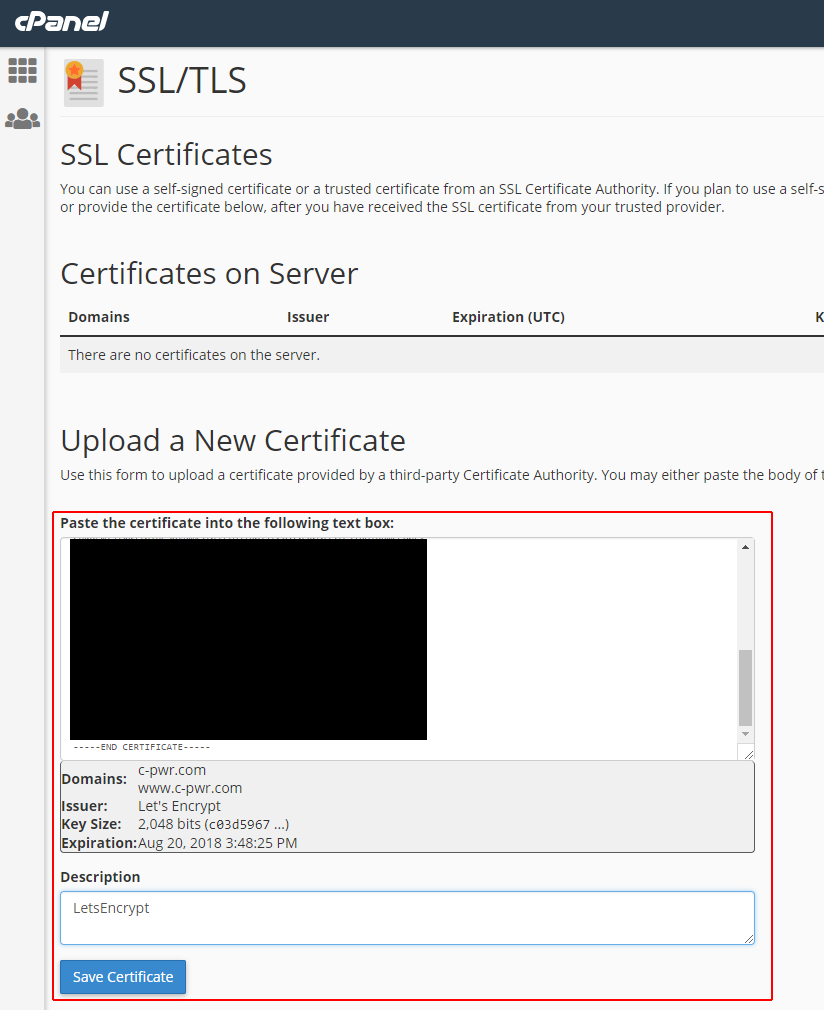
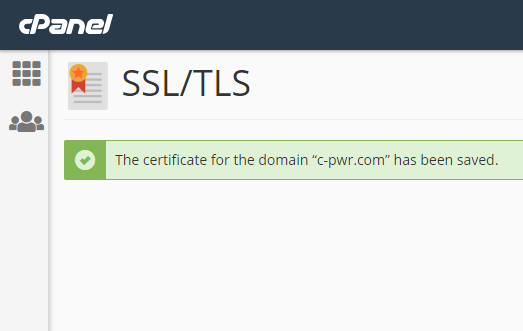
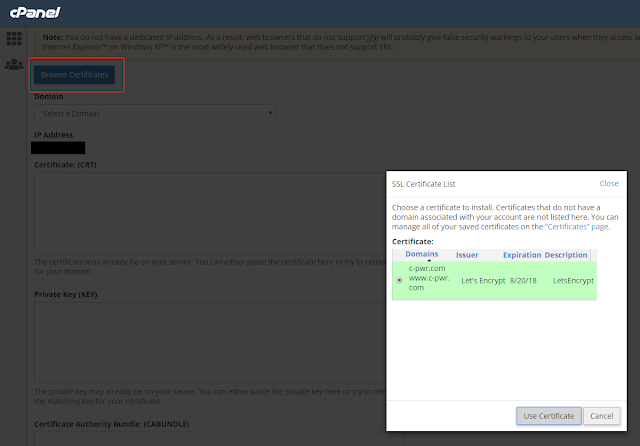
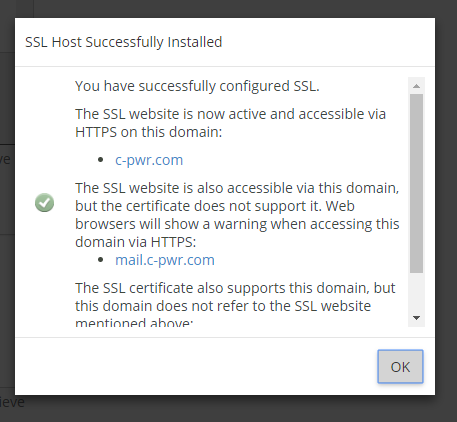
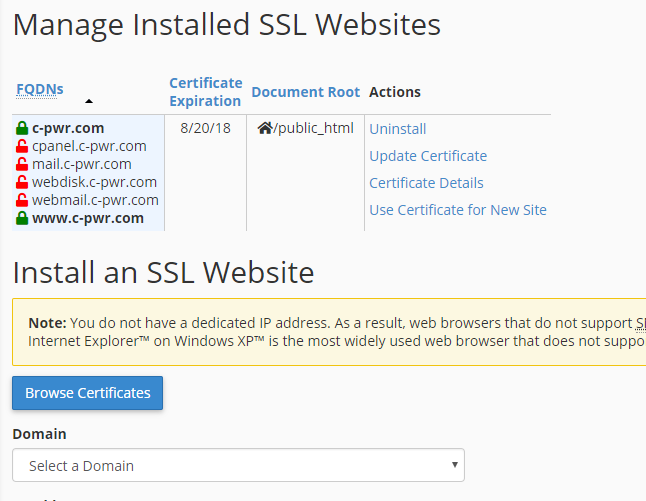
After this, I head over to the Manage SSL Sites tool and install this certificate as-is. It automatically detects the domains I specified in the original certbot command and applies the certificate to them.
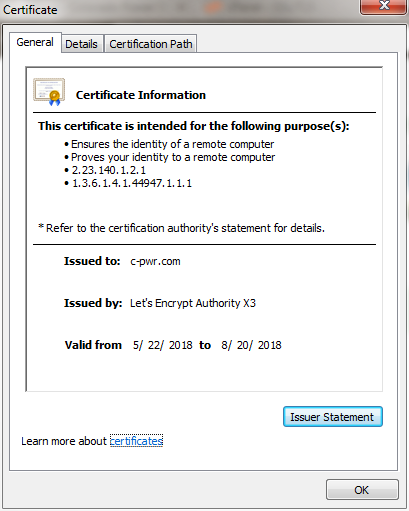
Renewal
At this point, I have no idea how the renew will work. Since LetsEncrypt issues certificate signatures for only 3 months, this will become an issue sometime in August. I HOPE the acme-challenges will remain the same, but if they don’t, it should be a simple task to recreate the files as above, then copy the files in manually, assuming certificates and private keys can be edited once created in cPanel.
Renewing is super simple, but with this method must be run differently from an automated certbot renew.
- Try
certbot renew. - An error message saying to run certonly may be displayed. If this is the case, run
certbot certonly -d c-pwr.com,www.c-pwr.comand specify what sort of ACME setup you want to run from (Apache may be preferrable and is confirmed to work for ppsstudios on 9/21/21). - If automatic ACME CA challenges are not working, try
certbot certonly -d c-pwr.com,www.c-pwr.com --manualand set up the text files manually. This has worked reliably since this article was first created. - I am asked to create new acme challenges on the webserver which I did.
- Since the cert already existed in the /etc/letsencrypt/live, it detected this as a renew, and did not prompt me to upload certificates a second time!!
- I logged into cPanel and created two text docs in the File Manager as instructed, hit enter in my local server command line and it did everything from there.
- 2018-08-01: I forgot that I also need to update and re-copy cert.pem and privkey.pem to CPanel SSL/TLS Status in order for it to actually update, as cPanel just emailed and said my cert was expiring in ten days.
- cPanel > SSL/TLS > Install and Manage (Manage SSL Sites)
- Scroll down and select the old domain in the dropdown.
sudo cat /etc/letsencrypt/live/c-pwr.com/cert.pemsudo cat /etc/letsencrypt/live/c-pwr.com/privkey.pem- Copy the certificate and private key text to the crt and key fields in cPanel.
- Click Install Certificate.
Additionally, I needed to manually set up my .htaccess file to redirect any http requests to the https version. This is usually done automatically by certbot during an automatic installation, and is embedded in the /etc/apache2/sites-available/000-default.conf file, but since I don’t have access to this, .htaccess will have to do.
Leave a Reply
You must be logged in to post a comment.